Be One with your Business, while HPE StoreEasy Manages your Data

Your organization faces constant challenges, so why should your data management also do it?
With Westham Trade and HPE StoreEasy find the right balance for your business between the efficiency you are looking for and a viable level of investment. With HPE StoreEasy you can have it all! file storage ranging from documents and images to audio and/or video files.
Flexible, efficient and reliable, the right size for the needs and budget of your organization, without compromising quality or functionality.

Strengthen your organization’s defenses by making data security everyone’s business
Protect your data with storage that has security designed in from the start
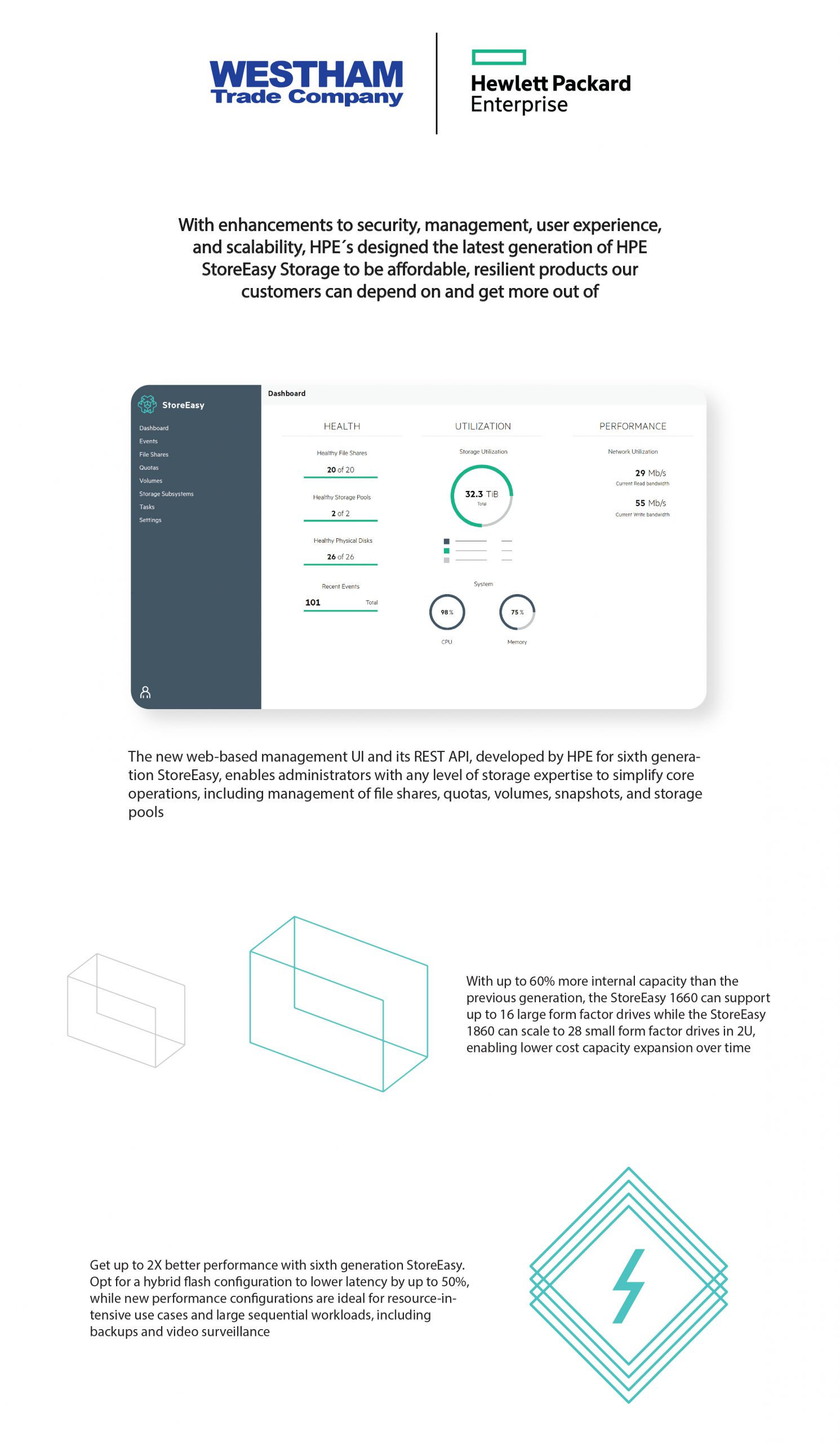
With the new sixth generation of HPE StoreEasy Storage, your organization can gain flexible, aordable network-attached storage and a secure baseline that saves you time, money, and eort. Built from the world’s most secure industry standard servers4 and tailored for storing file and application data, HPE StoreEasy Storage can help you reduce vulnerabilities through unparalleled protection, detection, and recovery capabilities included standard.
Managing Sensitive & Confidential Data
Limiting excessive access privileges narrows the playing field for bad actors while protecting your organization from inside threats. With StoreEasy’s advanced file management capabilities, you can automatically secure sensitive data by preventing unauthorized users from viewing, modifying, and distributing classified data.
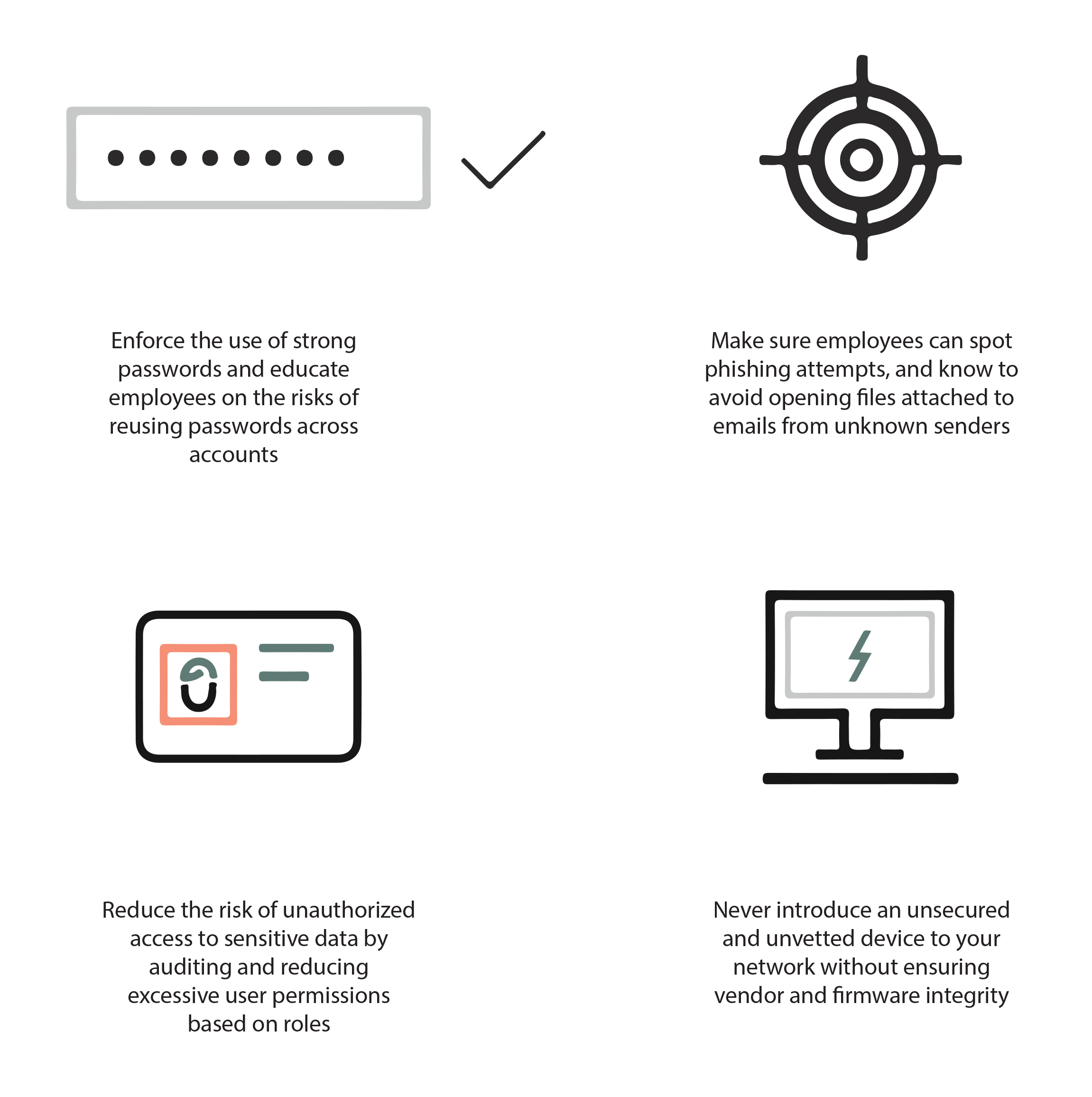
- Enforce the use of strong passwords and educate employees on the risks of reusing passwords across accounts
- Make sure employees can spot phishing attempts, and know to avoid opening files attached to emails from unknown senders
- Reduce the risk of unauthorized access to sensitive data by auditing and reducing excessive user permissions based on roles
- Never introduce an unsecured and unvetted device to your network without ensuring vendor and firmware integrity
Organizations consider malicious or deliberate insider attacks to be the most likely breach to impact their business.
When data is encrypted at rest using cloud file storage, organizations don’t hold the encryption keys - their cloud provider does.
Over 4,000 ransomware attacks occur every day, due to users opening compromised files, which execute malicious code & encrypts their data.
Here at Westham Trade we are more than committed to assist you on anything you may need.
Don´t Hesitate on contacting us
3620 NW 114 AVE DORAL, FLORIDA 33178
Direct Line (786) 464-5285/5303/5311
WWW.WTRADE.COM
#wtrade