EDGE TO CLOUD SECURITY
WAN and Security Architectures
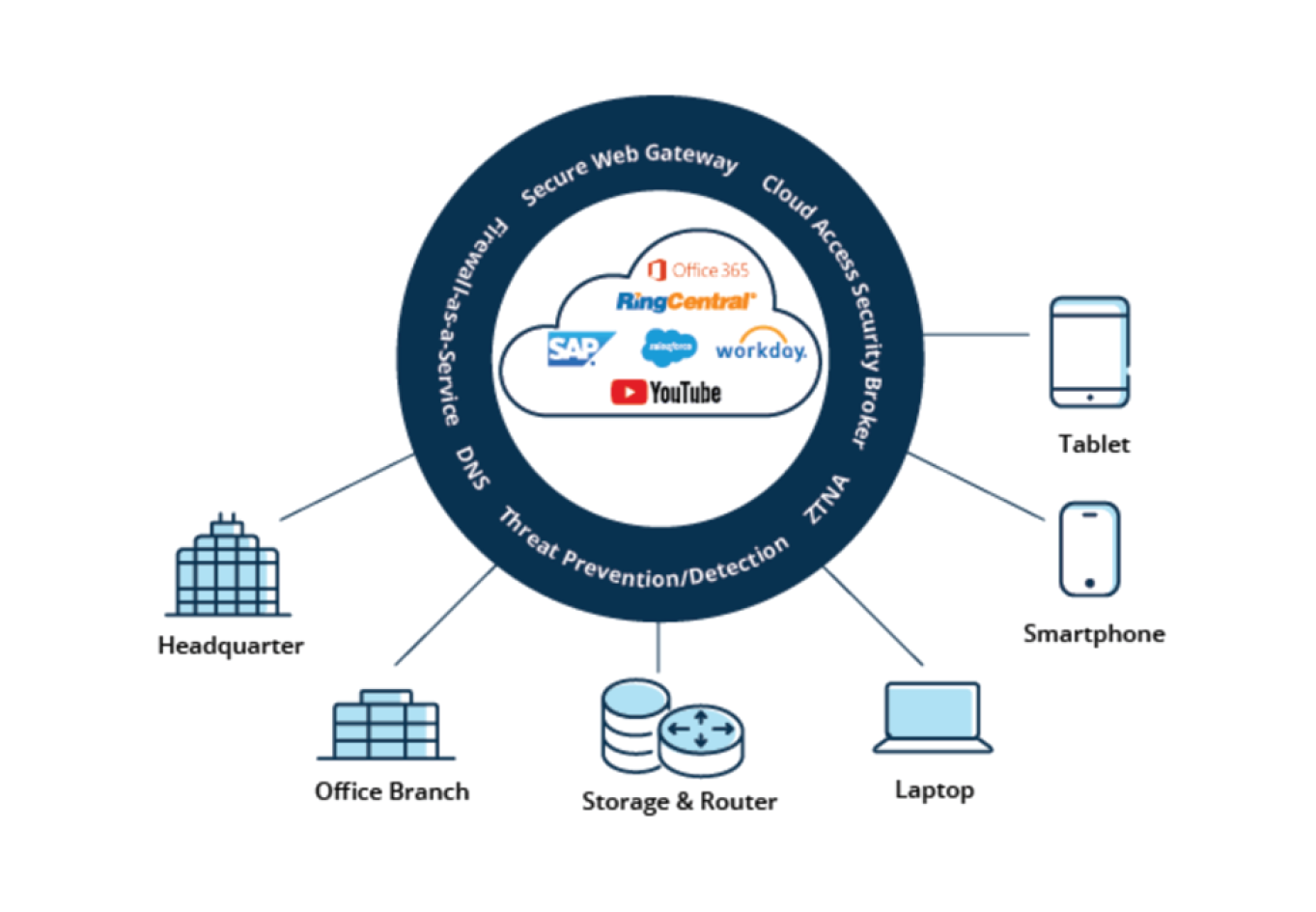
SASE is the combination of an advanced SD-WAN edge deployed at the branch and comprehensive cloud-delivered security services.
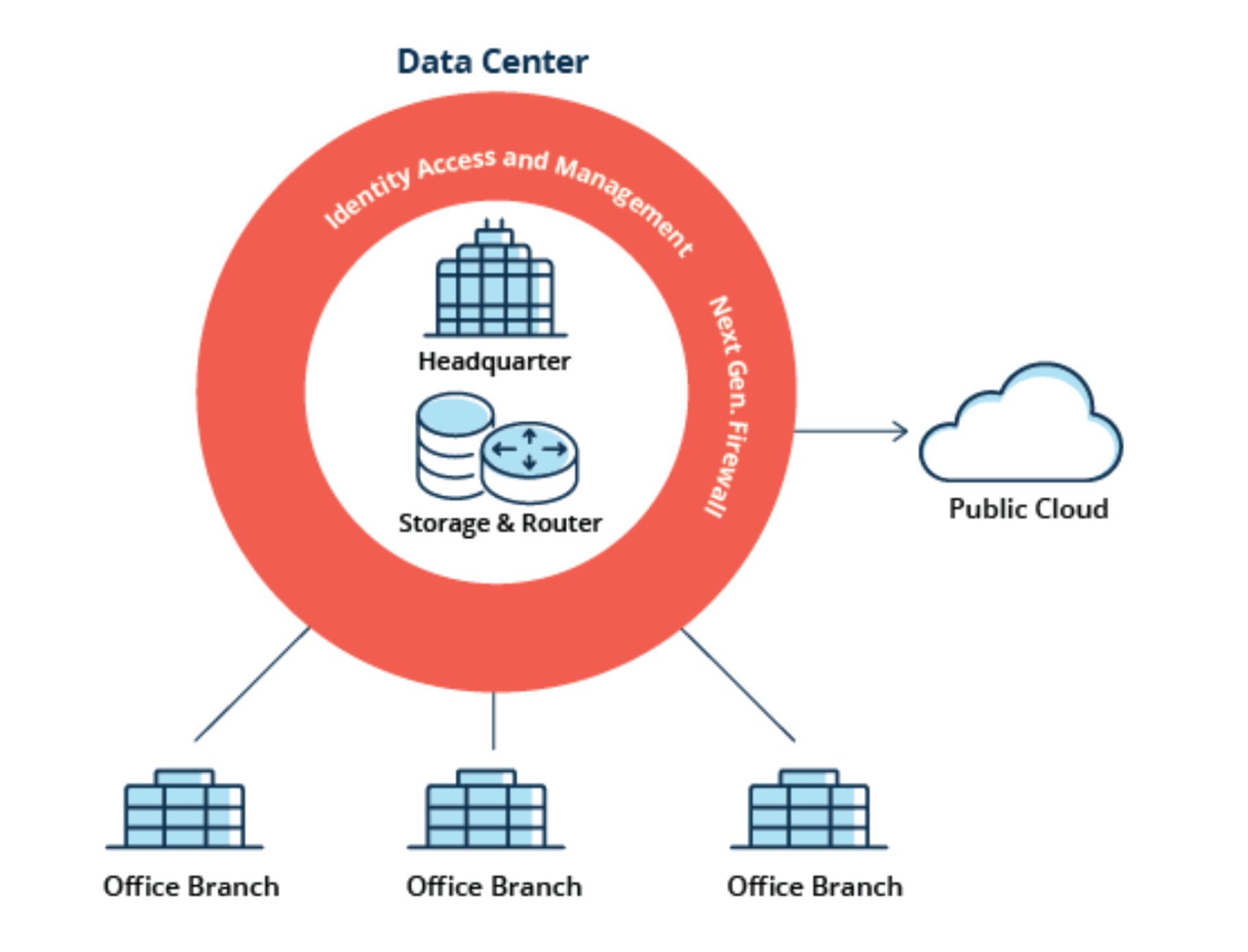
Traditionally, all application traffic from branch locations traversed over private MPLS services to the corporate data center for security inspection and verification. This architecture was appropriate when applications were hosted exclusively in the corporate data center. Now that applications and services have migrated to the cloud, the traditional network architecture falls short. Because internet- destined traffic must first traverse through the data center and corporate firewall before reaching its destination, application performance and user experience suffers.
To realize the full promise of digital transformation enterprises will need to transform both their WAN and security architectures. SASE is the convergence of SD-WAN edge and cloud-delivered security capabilities. Advanced SD-WAN capabilities integrated with modern cloud-delivered security services ensures consistent policy enforcement and access control for users, devices, applications, and IoT.
An enterprise can start with modernizing its WAN or its security, but to realize the true value of cloud investments, both must ultimately be addressed.